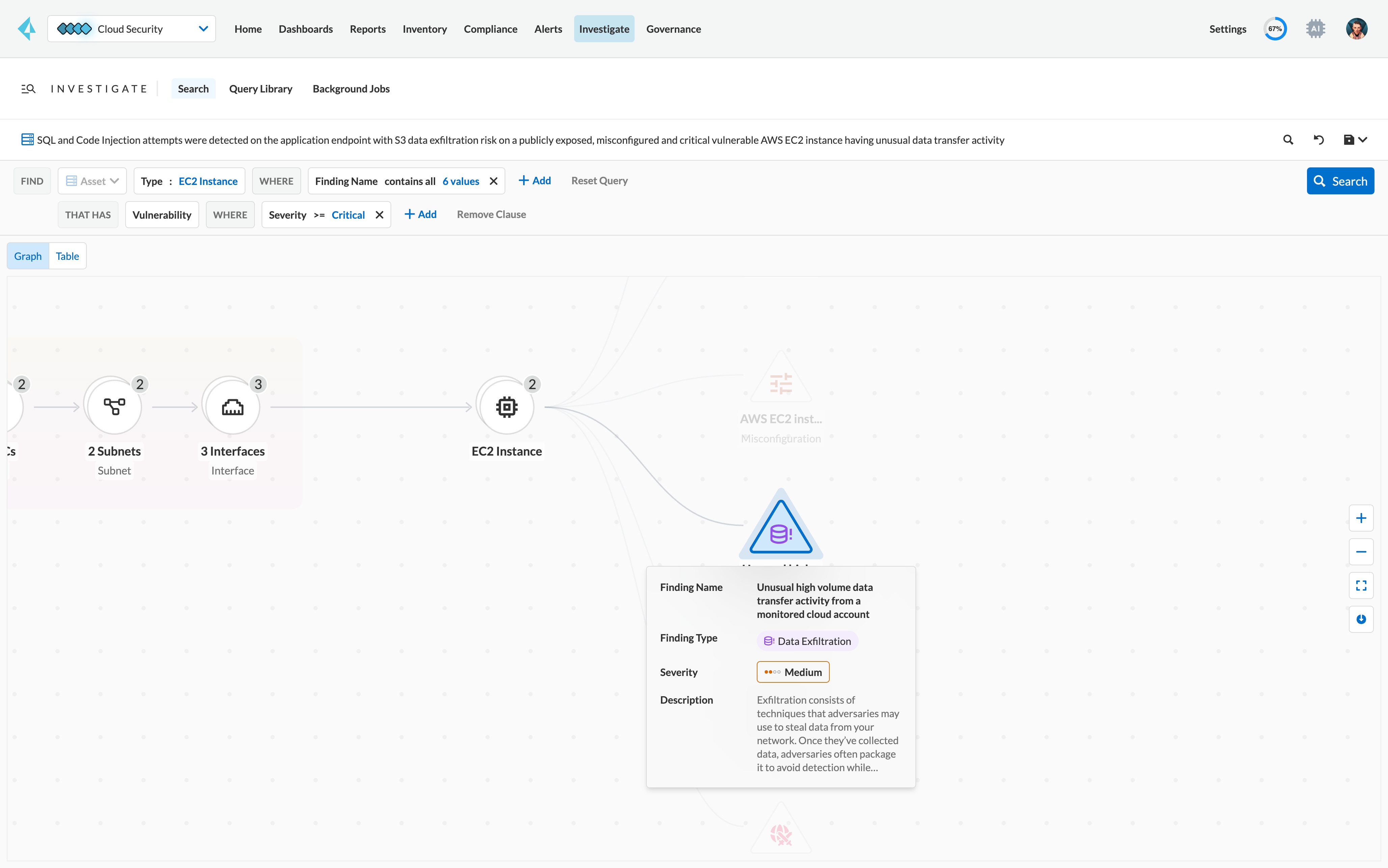
ML-based network anomaly detection
Prisma Cloud employs advanced ML to learn normal network behavior of each customer’s cloud environment to detect network anomalies and zero-day attacks effectively with minimal false positives.
Port scan and sweep detection
Detect common reconnaissance techniques per MITRE ATT&CK Cloud Matrix to facilitate remediation activities such as closing ports opened unintentionally.
Unusual port and server activity detection
Spot unusual activities which adversaries typically employ to evade detection while looking for critical assets such as PII, financial information and others in preparation for data exfiltration.
DNS threat detection
Identify threats attempting to exploit your network with DNS-based attacks such as domain generation algorithm (DGA) and cryptomining – all without changing your DNS infrastructure.