Highly accurate and context-aware
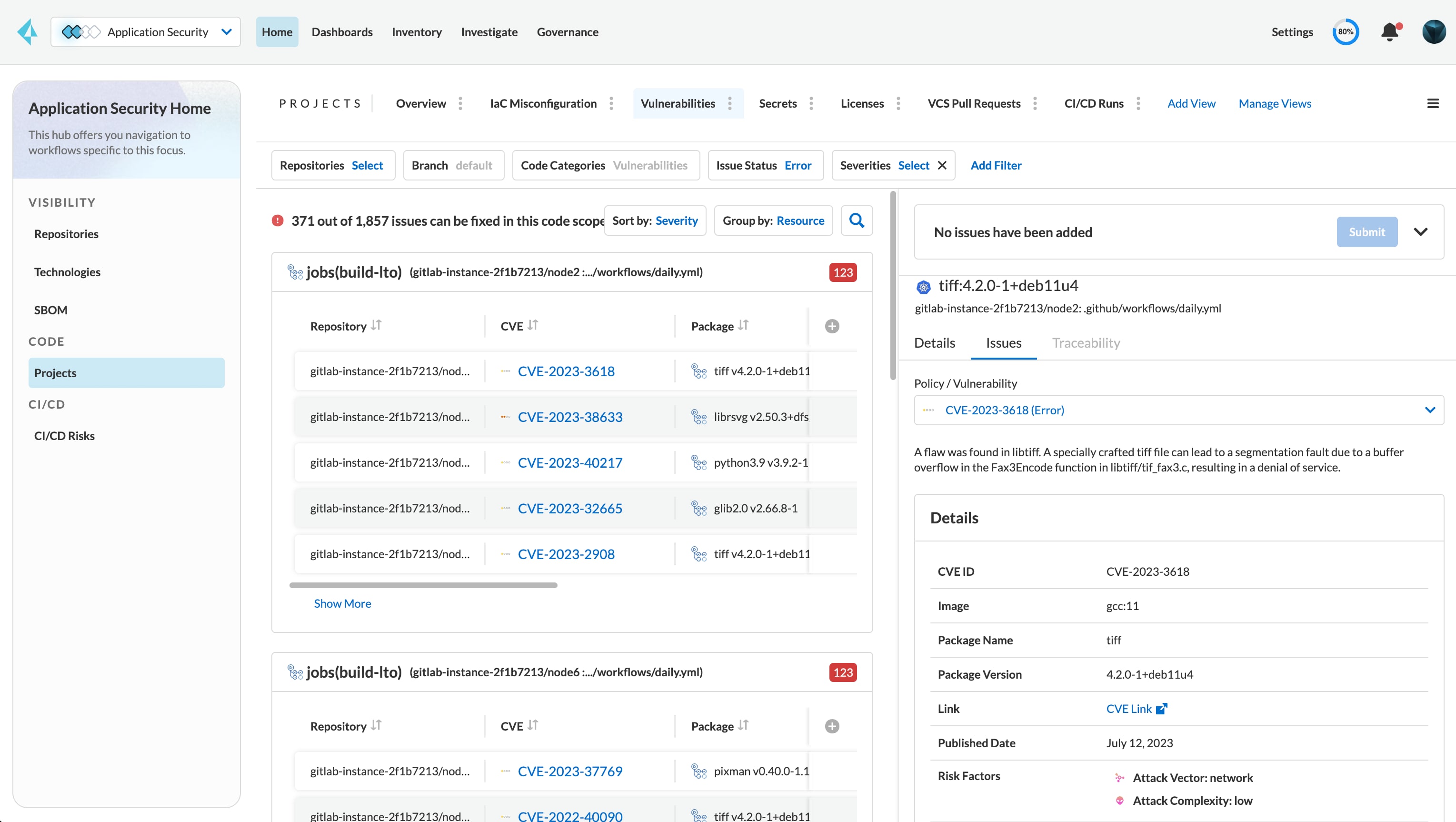
Built on top of the most reputable vulnerability databases and connected to the industry’s most robust infrastructure policy database, Prisma Cloud Software Composition Analysis (SCA) surfaces vulnerabilities with the context developers need to understand risk and implement fixes fast. Prisma Cloud provides the breadth and depth of open source coverage you need to stop the next big vulnerability in its tracks:
Scan across languages and package managers with unmatched accuracy
Identify vulnerabilities in open source packages with support for all the most popular languages and more than 30 upstream data sources to minimize false positives.
Leverage industry-leading sources for complete open source security confidence
Prisma Cloud scans open source dependencies wherever they are and compares them against public databases like NVD and the Prisma Cloud Intelligence Stream to identify vulnerabilities and surface important fix information.
Connect infrastructure and application risks
Narrow in on vulnerabilities that are actually exposed within your codebase to combat false positives and prioritize remediations faster.
Identify vulnerabilities at any dependency depth
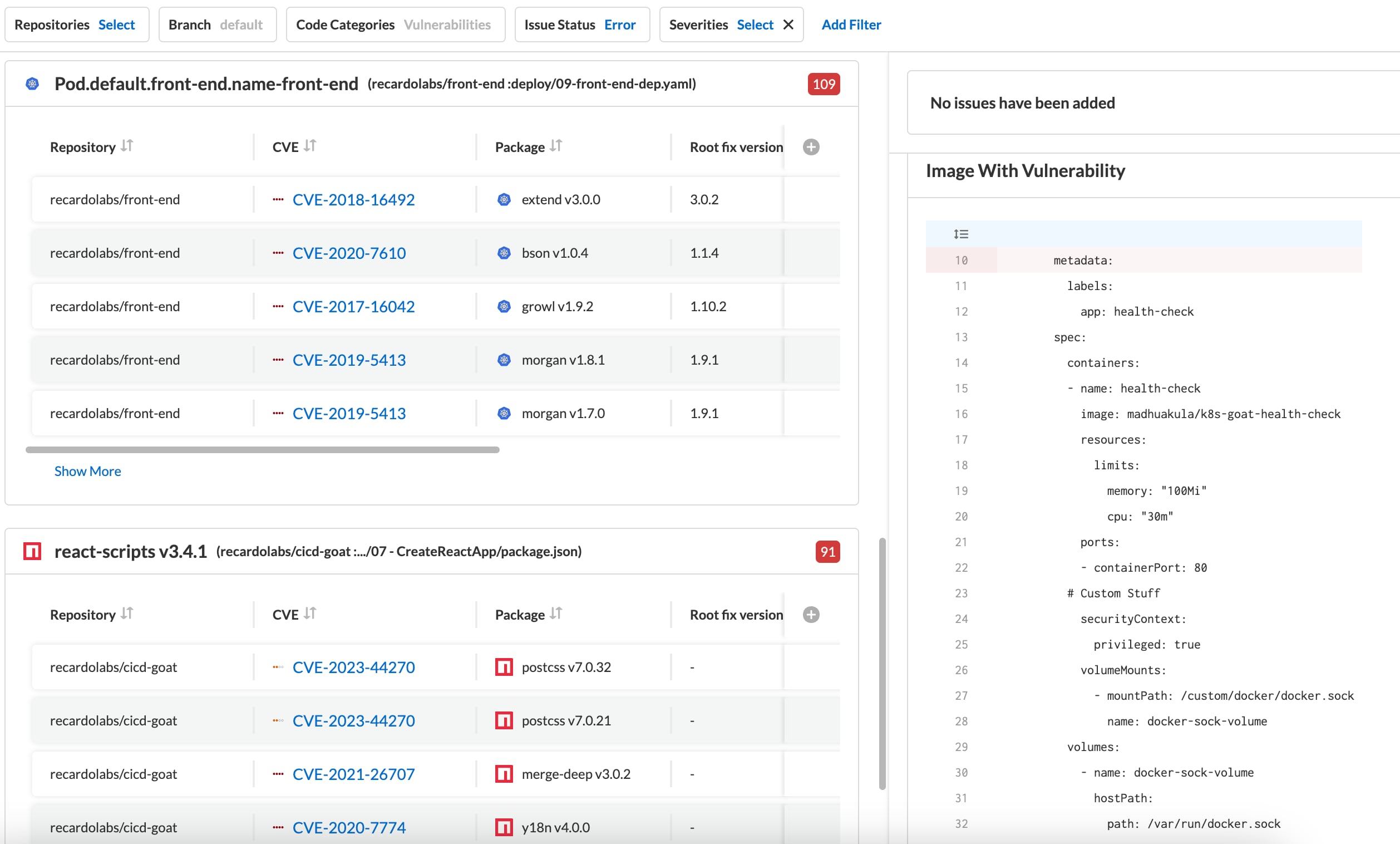
Prisma Cloud ingests package manager data to extrapolate dependency trees to the furthest layer to identify open source risk hidden from view.
Visualize and catalog your software supply chain
The Supply Chain Graph provides a consolidated inventory of your pipelines and code. With a visualization of all these connections as well the ability to generate a software bill of materials (SBOM), it’s easier to keep track of application risk and understand your attack surface.