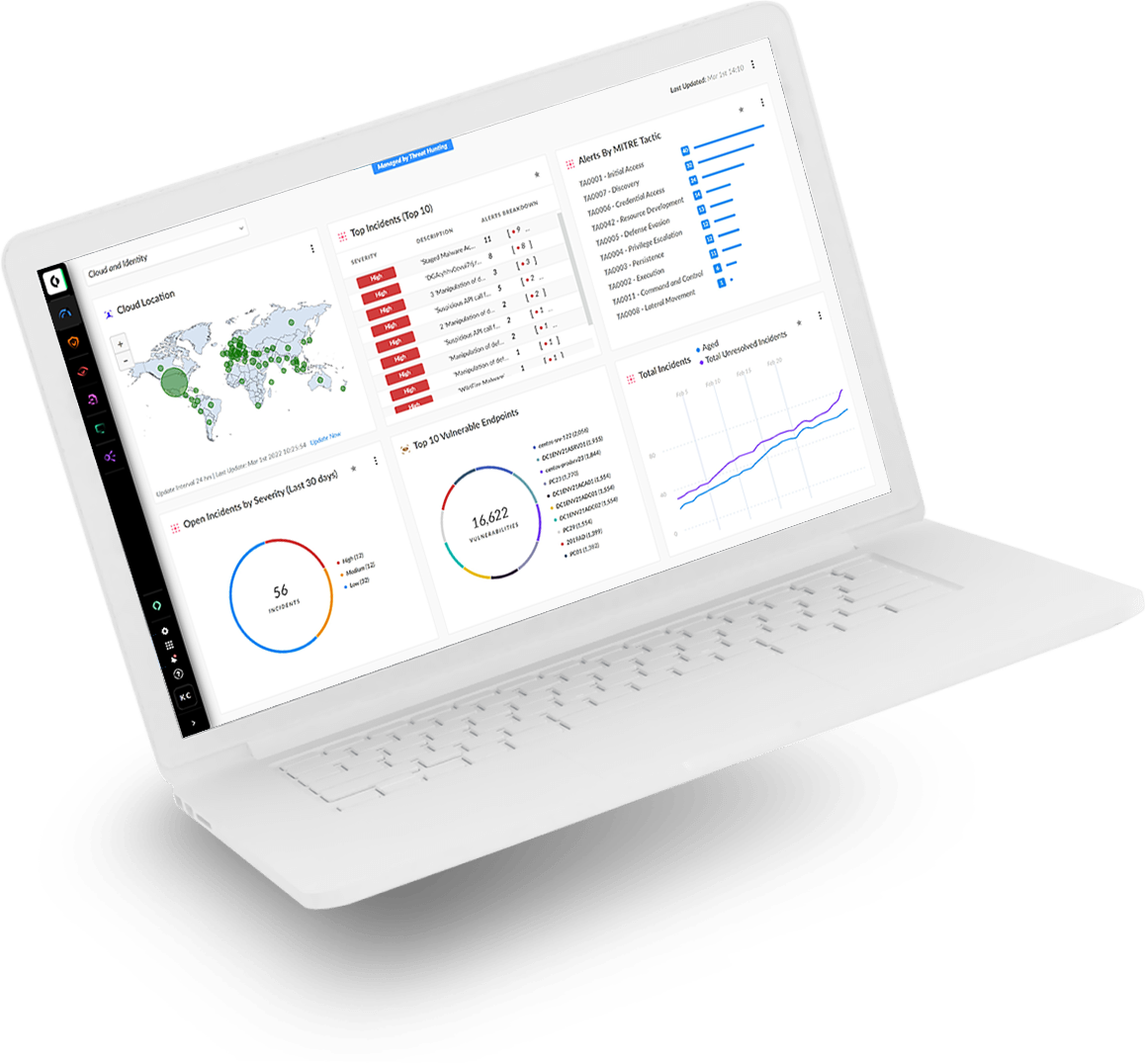
Cortex XDR is by far the smarter choice to stop modern threats.
SentinelOne’s Singularity™ approaches XDR with a one-size-fits-all solution, leaving organizations vulnerable to advanced threats. It simply lacks deep visibility and enterprise-ready features such as remote execution support for Python scripts, the preferred language for incident response tasks.
Cortex XDR excels far beyond. One simply has to look at performance in the 2023 MITRE Engenuity ATT&CK Evaluations (Turla). In fact, we outperformed all XDR vendors. How do we do this? Keep reading.

Real XDR
Cortex XDR delivers 15.3% more technique-level detections — the highest level of detections possible — than SentinelOne because it can continuously process the threat-level data that provides the context to answer why an adversary performed an action. The results from the 2023 MITRE ATT&CK Evaluations (Turla), which pitted XDR products against network implants and backdoors used by Russia’s Federal Security Service, further revealed that Cortex XDR outperformed SentinelOne in analytic detections, with 100% vs. 91.6%, and in blocking substeps, with 100% vs. 97.7%.
SentinelOne's XDR solution has some key limitations, mainly its heavy reliance on endpoint agents and data, and the lack of native forensic capabilities and visibility into unprotected endpoints. This approach may leave security teams without a complete overview, which is crucial for effective XDR.
Cortex XDR automates advanced stitching and customizable correlation rules so that alerts are efficiently grouped, managed and resolved as distinct incidents. It integrates network, cloud, identity and third-party data for comprehensive security across many complex environments. It’s why 6,000+ organizations worldwide count on the industry’s first true XDR.
- Cortex XDR advances security beyond just endpoint protection and data collection, integrating native network, cloud, identity and third-party data to stop modern cyberattacks.
- Data from any source is automatically stitched together to reveal the root cause and timeline of alerts to identify and quickly put a stop to threats.

SentinelOne’s lack of critical features slows incident response.
Several capabilities are needed to pinpoint anomalous behavior and enable quick investigation of alerts. For example, without integrated cloud sandboxing and real-time file analysis, SentinelOne customers may be exposed to new forms of malware. When they outsource sandboxing, it causes increased cost, limited dynamic analysis and manual upload of samples to the cloud.
Meanwhile, Cortex XDR runs operations on its data lake, making it easier to detect advanced threats and apply user entity and behavior analytics . Plus, we’ve seamlessly integrated WildFire®, the industry-leading dynamic malware analysis sandbox. This means file submissions and verdicts are delivered automatically. Overall, Cortex XDR’s robust features enhance threat detection and threat intelligence, enabling fast, effective incident response.
- Integration with our WildFire malware prevention service goes beyond traditional sandboxing to detect unknown threats in a complete cloud analysis environment.
- Behavioral analytics analyzes data by tracking more than 1,000 behavior attributes to profile behavior and detect malicious activity.
- Host Insights combines vulnerability assessment, application and system visibility, along with a powerful Search and Destroy feature to help identify and contain threats across all endpoints.

SentinelOne’s lack of customization hurts enterprise readiness.
Different operating systems have unique configurations, security needs and vulnerabilities. The rigid, inflexible structure of SentinelOne may not handle the requirements of each OS — or the demands of each SOC. Additionally, SentinelOne does not provide a natively integrated forensics module for macOS devices. This is crucial due to the growing use of macOS in business settings and its unique security challenges.
In stark contrast, Cortex XDR significantly enhances security with a flexible management system. It adeptly groups, manages and resolves related alerts as single incidents, reducing alerts by an astounding 98%.*
*Based on an analysis of Cortex XDR customer environments.
- With a single click, analysts can instantly reveal the root cause, reputation and sequence of events, lowering the experience needed to verify threats.
- Customizable correlation rules allow analysts to define rules based on dozens of different parameters to help identify misuse of systems and applications and thwart evasion techniques.
Compare Cortex XDR to SentinelOne
| Products | SentinelOne | Cortex XDR |
|---|---|---|
| Real XDR | Lacks the full picture
| Broader visibility
|
|
| |
| ||
| Critical Feature Set | Fragmented solution
| Full and flexible features
|
|
| |
| ||
| Incident Management | Disconnected alerts
| Efficient, high-performance automation
|
|
| |
|
* Based on an analysis of Cortex XDR customer environments.
** Palo Alto Networks SOC analysis showing reduced investigation time from 40 minutes to 5 minutes.